I have a UPS (APC BK650) to supply power for my OpenWrt router, Network switch and Wireless AP. Since the UPS has no indicator screen, i can’t check its running status(Load, Battery runtime), that’s a little unacceptable for me.
Then i spent some time googling and deployed NUT (Network UPS Tools) on the OpenWrt router, which provides a simple web page showing status of connected UPS.
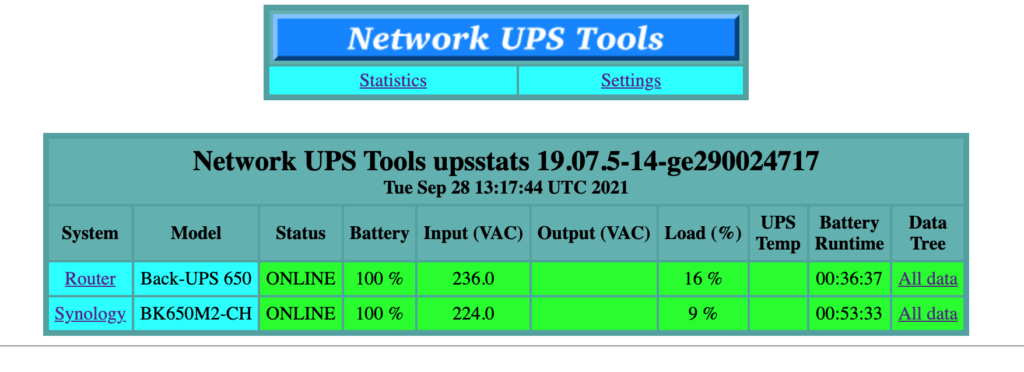
Here is my installation and configuration process:
1. Install NUT and dependences
opkg install nut nut-common nut-driver-usbhid-ups nut-server nut-upsc nut-web-cgi usbutils- nut nut-common nut-server basic packages
- nut-driver-usbhid-ups nut driver compatible with APC BK650
- nut-upsc provides
upsccommand - nut-web-cgi provides a web status page
- usbutils provides
lsusbcommand
2. Configure NUT server, edit /etc/config/nut_server
config driver 'apc'
# APC BK650 is compatible with the usbhid driver
option driver usbhid-ups
# auto detect USB port
option port auto
config listen_address
option ::1
config upsd upsdReload nut server
/etc/init.d/nut-server reload3. Configure the status web page, edit /etc/config/nut_cgi (Skip this step If you just want to check UPS status by upsc command)
# Local UPS configured at /etc/config/nut_server
config host
option upsname apc
option hostname localhost
option displayname "Router"
# This is my another UPS connected with Synology NAS
# You can just ignore this section
config host
option upsname ups
option hostname 192.168.100.99
option displayname "Synology"
config upsset
option enable 0Reload nut cgi
/etc/init.d/nut-cgi reload5. Connect UPS and OpenWrt router with a USB cable
6. Check if the UPS has been detected
root@OpenWrt:~# lsusb
Bus 002 Device 001: ID 1d6b:0003 Linux Foundation 3.0 root hub
Bus 001 Device 002: ID 051d:0002 American Power Conversion Uninterruptible Power Supply
Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
root@OpenWrt:~# ps ax|grep usbhid
2753 pts/1 S+ 0:00 grep usbhid
2865 ? Sl 111:50 /lib/nut/usbhid-ups -D -a apc -u nutThe UPS device should appear in output of lsusb, and usbhid-ups process will also start automatically.
7. If everything goes well, you can get UPS status by command upsc, or visit status web page at http://your router ip/nut/ (if nut-cgi installed),
root@OpenWrt:~# upsc apc
battery.charge: 100
battery.charge.low: 10
battery.charge.warning: 50
battery.date: not set
battery.mfr.date: 2018/10/05
battery.runtime: 2197
battery.runtime.low: 120
battery.type: PbAc
battery.voltage: 13.6
battery.voltage.nominal: 12.0
device.mfr: APC
device.model: Back-UPS 650
device.serial: 3B1840X68970
device.type: ups
driver.name: usbhid-ups
driver.parameter.pollfreq: 30
driver.parameter.pollinterval: 2
driver.parameter.port: auto
driver.parameter.synchronous: no
driver.version: 19.07.5-14-ge290024717
driver.version.data: APC HID 0.96
driver.version.internal: 0.41
input.sensitivity: low
input.transfer.high: 266
input.transfer.low: 165
input.transfer.reason: input voltage out of range
input.voltage: 232.0
input.voltage.nominal: 220
ups.beeper.status: enabled
ups.delay.shutdown: 20
ups.firmware: 822.A3.I
ups.firmware.aux: A3
ups.load: 16
ups.mfr: APC
ups.mfr.date: 2018/10/05
ups.model: Back-UPS 650
ups.productid: 0002
ups.serial: 3B1840X68970
ups.status: OL
ups.timer.reboot: 0
ups.timer.shutdown: -1
ups.vendorid: 051d